In an increasingly interconnected world, airports, power plants, and urban infrastructure face unique cybersecurity challenges that can have significant impact on national security, economy, and human safety. Airports, as critical hubs of global transportation, must safeguard against sophisticated threats targeting flight operations, passenger data, and communication systems, ensuring the security and efficiency of air travel. Power plants, the backbone of energy supply, are prime targets for cyber-attacks that can lead to widespread power outages, jeopardize public safety, and impact the economy. Urban infrastructure, with its complex network of public services, is vulnerable to cyber-attacks that can disrupt daily life, compromise public safety, and lead to financial losses.
The Challenge: Evolving Security Operations Needs
-

Complex Threat Landscape
Cyber attackers are employing increasingly sophisticated tactics, techniques, and procedures, making traditional defense mechanisms obsolete.
-
Expanding Attack Surface
The proliferation of IoT/OT devices, cloud applications, and remote work environments along with vast and varied networks within airports, power plants, and urban infrastructure has dramatically increased potential entry points for attackers.
-

Complexity and Integration
Difficulty in integrating diverse systems and technologies across large, complex environments.
-

Legacy Systems
Challenges in securing outdated and legacy systems which are still in operation.
-

Alert Overload
Traditional security solutions generate a constant stream of low-fidelity alerts, forcing analysts to shift through false positives and miss critical threats.
-

Skills Shortage
The cybersecurity industry faces a critical shortage of skilled professionals, leaving many security operations centers (SOCs) understaffed and overwhelmed.
-

Compliance and Regulations
Difficulty in meeting stringent regulatory requirements and industry standards.
About gramax.ai platform
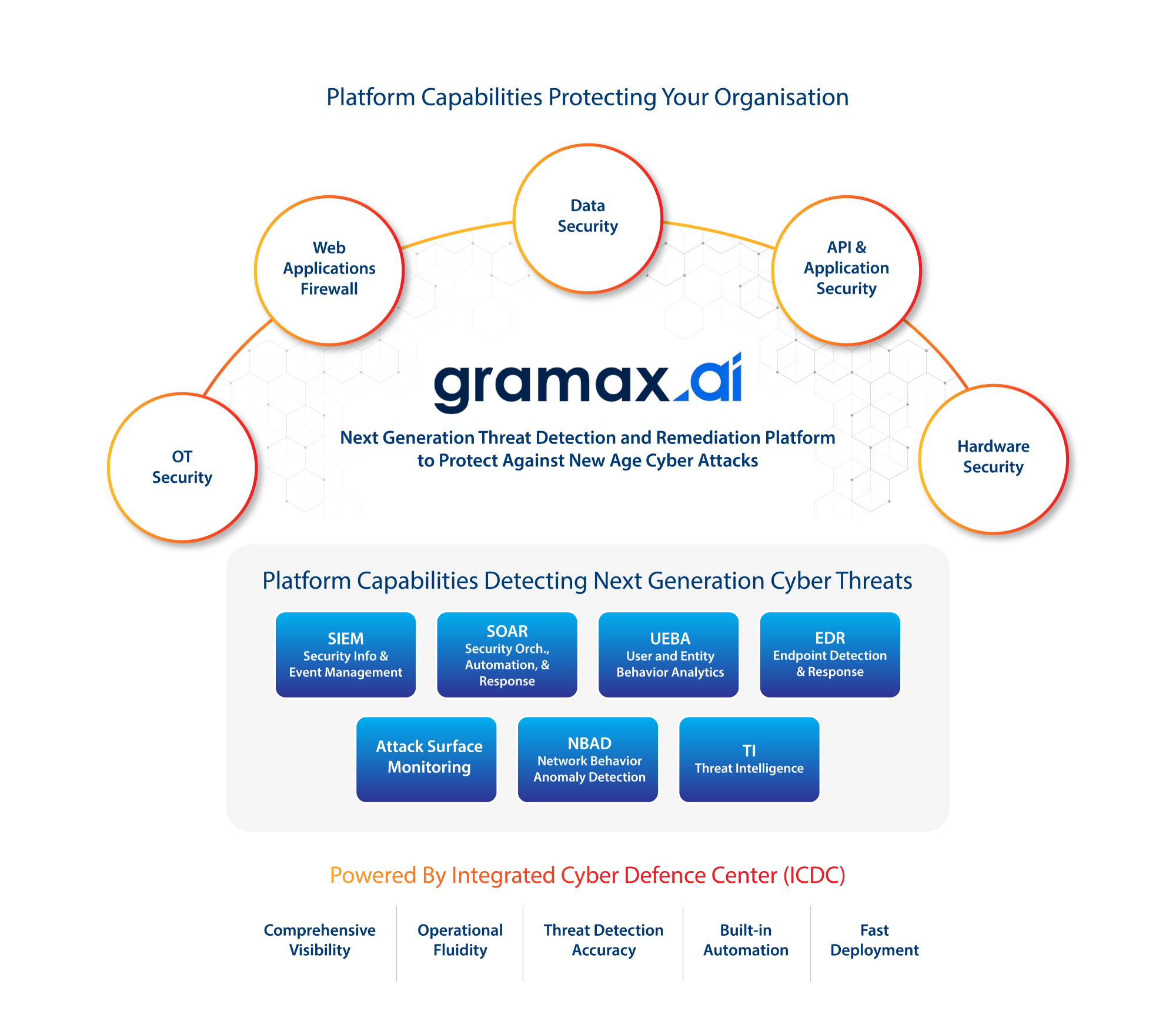
gramax.ai is our comprehensive platform for Next Generation Threat Detection and Remediation that guards against cutting-edge cyberattacks. The platform goes beyond static rules and augments human intelligence by processing massive datasets using AI and automation, enabling it to detect threats and risks that might go unnoticed.
-
 A Vision for Unified Security
A Vision for Unified Securitygramax.ai is a cybersecurity vision for the future of converged information technology, operational technology (IT and OT) and physical realms. The platform incorporates specialized modules for OT security with essential IT security components like SIEM, UEBA, EDR, and SOAR ...
-
 Augmenting Human Intelligence
Augmenting Human IntelligenceThe user-friendly interface and AI-assisted investigations will boost your team's productivity and reduce the learning curve. Additionally, you may supplement your internal resources with superior knowledge on demand by using our Integrated Cyber Defence Centre (ICDC) service...
-
 True automation
True automationgramax.ai takes an automation-first approach to incident remediation. Our platform features alert-specific playbooks that trigger automatically, addressing risks before an analyst needs to get involved. Moreover, gramax.ai learns from manual analyst actions, continuously improving...
-
 True Synergy across Modules
True Synergy across ModulesUnlike cobbled-together solutions, gramax.ai offers authentic integration. Our Unified Security Event Model ensures that all components work in harmony, sharing critical intelligence and presenting a coherent view of your security posture. This synergy dramatically...
A closer look on key capabilities integrated in gramax.ai
gramax.ai combines the 'detection' and "protection" capabilities into a single unified platform.
The 'detection' capabilities are as follows:
- Security Information and Event Management (SIEM) Provides comprehensive log management, correlation, alerting, and compliance reporting to enhance visibility and streamline security operations.
- Security Orchestration, Automation, and Response (SOAR) Features a robust SOAR module that enables the creation and automation of incident response playbooks, reducing the response time and improving efficiency.
- User and Entity Behavior Analytics (UEBA) Utilizes machine learning and behavioral analysis to profile users and entities, identifying and alerting on abnormal behaviors that may indicate security threats.
- Endpoint Detection and Response (EDR) Delivers advanced endpoint security through a combination of endpoint agents and cloud-based analytics, ensuring threat prevention, automated responses, and detailed telemetry for thorough investigations.
- Network Behavior Anomaly Detection (NBAD) Monitors network traffic for unusual patterns that could signify malicious activity, enhancing the ability to detect and respond to network threats.
- Threat Intelligence (TI) Integrates multiple threat intelligence feeds, enriching alerts and incidents with contextual information to improve threat detection and response strategies.
gramax.ai also provides the following vital 'protection' capabilities:
- Web Application Firewall (WAF) Our Web Application Firewall (WAF) monitors and secures web applications from cyber threats including but not limited to HTTP traffic, protecting against threats like SQL injection and cross-site scripting (XSS). WAF also ensures the availability of your web applications, and maintains the integrity of your digital assets.
- Attack Surface Monitoring Attack Surface Monitoring (ASM) is vital to our cybersecurity services, continuously scanning an organization's digital footprint to identify vulnerabilities and potential attack vectors. Offering real-time visibility into exposed assets and risks, ASM helps clients proactively mitigate threats and strengthen their security posture.
- Data Security Our Data Security service offers comprehensive solutions to protect sensitive information throughout its lifecycle. With encryption, access control, data loss prevention, and secure disposal, we ensure your data remains confidential, integral, and available. These measures help you comply with regulations and safeguard your most valuable asset-data.
- API & Application Security Our API & Application Security service provides comprehensive protection against exploitable vulnerabilities. We conduct thorough security assessments, implement secure coding practices, and deploy advanced security measures to ensure the resilience and reliability of your APIs and applications.
- Hardware Security Hardware Security is a crucial part of our cybersecurity offerings. We deliver robust solutions to protect physical devices and components from tampering, unauthorized access, and other threats. Securing the hardware layer ensures the overall integrity and trustworthiness of your computing environment.
- Operational Technology (OT) Operational Technology (OT) Security is crucial for safeguarding critical infrastructure. Our service secures Industrial Control Systems (ICS), SCADA systems, and other OT environments against cyber threats with specialized measures tailored to their unique challenges, ensuring operational safety and continuity.
